Encrypt form submission data
Explains how to enable form data encryption with Azure Key Vault, authorize users to work with it, and how it impacts Optimizely Forms.
Note
Optimizely Forms is only supported by MVC-based websites and HTML5-compliant browsers.
By default, form submission data is stored as plain text. However, in some environments, the law requires data to be encrypted. For this reason, Optimizely Forms (version 4.6 and higher) includes a data encryption feature that can help clients meet strict legal requirements. Submission data can be encrypted before being saved into the database and decrypted later.
The algorithm key is the most crucial feature of data encryption. It needs to be ultimately secured for data safety. Optimizely Forms uses Azure Key Vault – a feature of the Azure platform, as the default algorithm key storage, which lets you separate administrators or IT staff from accessing the key like traditional servers. This significantly improves data security. Without Azure Key Vault, the feature still works well with other kinds of key storage, such as on-premises servers or SQL Server. The article Forms crypto engine explains how you can customize the crypto engine with different kinds of key storage or algorithms.
Note
Azure Key Vault is not included with Optimizely Digital Experience Platform (DXP) and cannot be purchased as an add-on. You can purchase your own Azure Key Vault and use it with your applications implementation.
Azure Key Vault
The default crypto engine of Optimizely Forms uses Azure Key Vault to store the symmetric algorithm key. It then retrieves the key from KeyVault and uses it for encryption and decryption. For information, see:
Data block and key size of a symmetric algorithm
Optimizely Forms uses the Advanced Encryption Standard (AES) to encrypt and decrypt data. AES has two main concepts:
- Data block size – Optimizely Forms follows the standard 128-bit length.
- Key size – Optimizely Forms supports three types: 128 bits, 192 bits, and 256 bits.
Azure Key Vault refers to its key as a "secret." To use encryption mode, create a secret on Azure Key Vault. Optimizely Forms retrieves your secret key from the Key Vault server and uses it in the encryption engine's symmetric algorithm. The secret should be base-64 encoded, meaning its characters are in the ASCII range of UTF8, and each character is 1 byte. So, the secret should contain only 16 characters for a key size of 128 bits, 24 for a key size of 192 bits, and 32 for a key size of 256 bits.
Configure encryption
To enable form data encryption, follow these steps.
Prerequisites
- A secret on Azure Key Vault.
- Installed NuGet package EPiServer.Forms.Crypto.AzureKeyVault.
- The session state is enabled.
-
Open the
Forms.configfile. -
Before the
<providers>section, add a\<storage defaultProvider="DdsEncryptedPermanentStorage">element.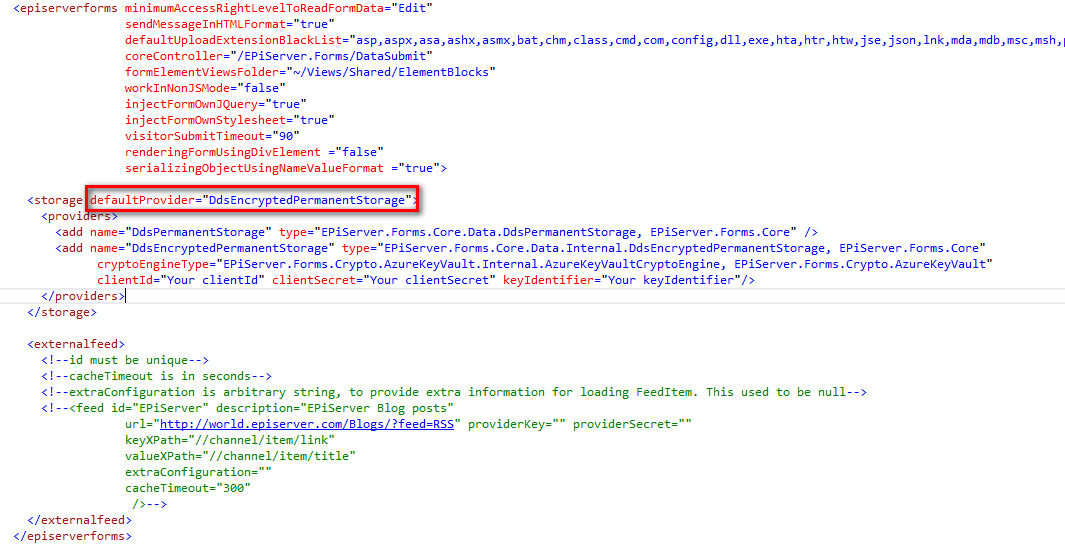
-
Within the
<providers>element, specify three Azure Key Vault–related parameters for the cryptographic engine.ClientId– Application ID registered with Azure Active Directory.ClientSecret– The key created for the application in Active Directory.KeyIdentifier– The endpoint used for communication with Azure Key Vault. Used to retrieve token access, public key retrieval, and data decryption.
-
Restart your site.
After you complete these steps, form data is encrypted before being saved (except system fields).
Sample Forms.config file excerpt:
<add name="DdsEncryptedPermanentStorage"
type="EPiServer.Forms.Core.Data.Internal.DdsEncryptedPermanentStorage, EPiServer.Forms.Core"
cryptoEngineType="EPiServer.Forms.Crypto.AzureKeyVault.Internal.AzureKeyVaultCryptoEngine, PiServer.Forms.Crypto.AzureKeyVault"
clientId="abnnnnn-nnnn-nnnn-nnnn-nnnnnnnnnnhi"
clientSecret="nnnnnnnnnnnnnnnnnnn/nnnnnnnnnnnnnA="
keyIdentifier="https://addonkeyvault.vault.azure.net/secrets/Thuy16Bytes/annnnnnnnnnnnnnnnnnnnnnnef"/>
Note
To return to Optimizely Forms default mode that does not encrypt data, set
DdsPermanentStorageas the storage element's default provider.
Set user access rights to encrypted form data
When you want certain users to access the Form Submissions view, which lets users see encrypted data and export decrypted data, create a role and assign to it the privileges eligible to access form data. Those privileges are defined in the minimumAccessRightLevelToReadFormData element of the Forms.config file for the Optimizely Forms folder, such as shown in the following example.
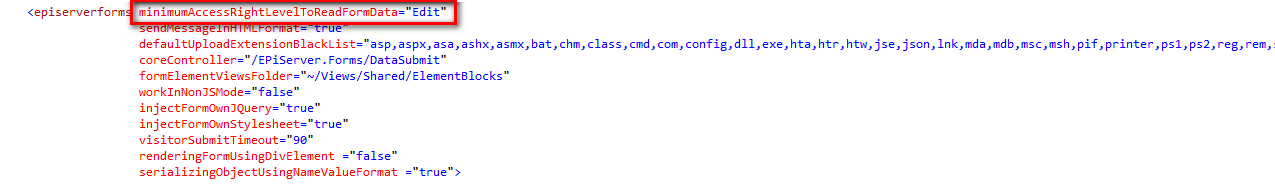
Next, assign the role to appropriate users.
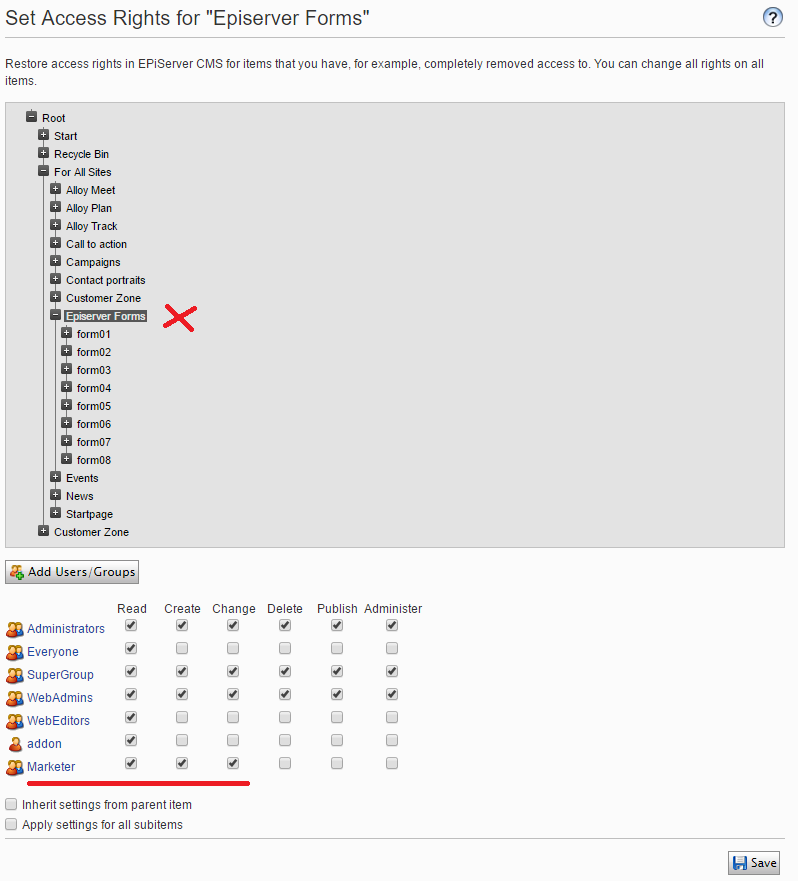
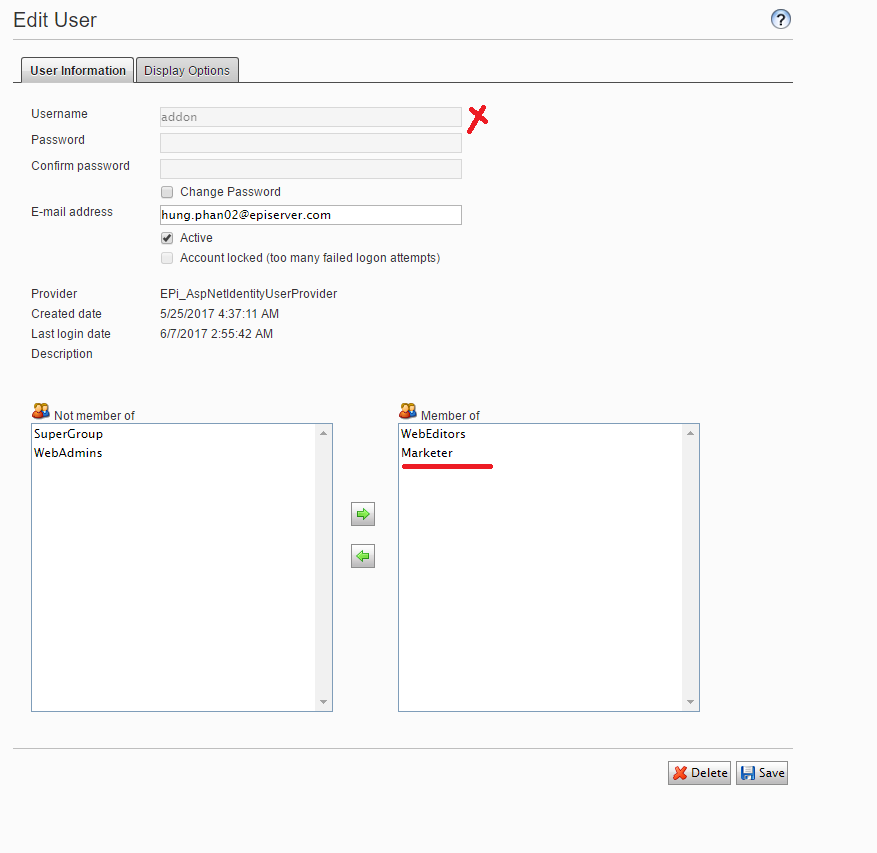
From this point, those users can view encrypted data and see an option to export as Decrypted CSV data.
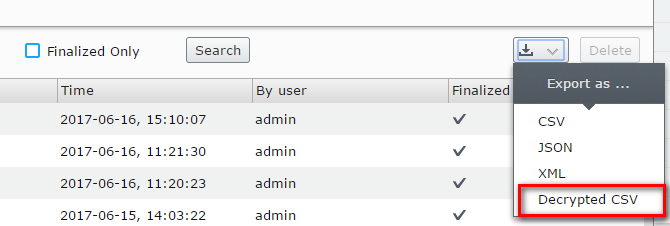
Decryption mode performance issues
Currently, the asynchronous export of decrypted CSV files is not supported. Because encryption is a time-consuming operation, if forms contain a large amount of data and the allowed time is too short, timeouts may occur. To use decryption more efficiently, you should increase your system timeout.
Impact on other functionality
Sort functionality
When using encryption mode, columns must have the string data type (except system columns). As a result, the sort functionality does not work because it is based on numeric data types.
Data storage
Normally, when a visitor clicks Next in a form, data is saved to the database. But in encryption mode, submission data is saved only when a user finalizes a submission, to enhance performance. Data must be encrypted before it is saved, and encryption is a resource-consuming operation.
Progress button
For performance and security reasons, the progress button does not work in encryption mode. If a session expires, users must refill form data from the beginning. Old data is removed.
Updated about 1 month ago